As businesses evolve in the digital landscape, the need for robust cybersecurity measures becomes paramount. With the rise of cloud computing and the increasing complexity of IT infrastructures, integrating cybersecurity with iPaaS (Integration Platform as a Service) has emerged as a critical strategy for safeguarding IT assets. In this comprehensive guide, we delve into the technical aspects of iPaaS and cybersecurity integration, exploring how this synergy fortifies defenses against cyber threats.
Aonflow iPaaS – Free for First 3 Months!
Build and run up to 1,500 transactions monthly with no cost. No payment info needed!
The Role of iPaaS in Cybersecurity
In the contemporary digital landscape, where every facet of business operates within a web of interconnected systems, cybersecurity transcends the mere protection of individual endpoints. It encompasses safeguarding the entirety of a network infrastructure against an array of threats lurking in the virtual realm. iPaaS emerges as a linchpin in this cybersecurity framework, wielding its capabilities to provide a centralized vantage point for overseeing and managing data flows across the organizational spectrum.
The essence of iPaaS lies in its ability to seamlessly integrate diverse applications, data streams, and systems, thereby facilitating the smooth exchange of information. This integration extends beyond mere convenience; it serves as the bedrock upon which robust cybersecurity measures can be implemented. By intertwining with a myriad of security tools and protocols, iPaaS platforms empower organizations with the means to establish and enforce uniform security policies throughout their digital domain.
Centralized visibility emerges as a cornerstone of iPaaS-enabled cybersecurity, affording organizations a panoramic view of data traversing their networks. This bird’s-eye perspective enables proactive monitoring of data transmissions, allowing for the timely detection of any aberrations or potential security breaches. Furthermore, iPaaS equips organizations with the tools necessary to swiftly respond to such incidents, thereby mitigating their impact and minimizing downtime.
Moreover, the integration of iPaaS with security protocols furnishes organizations with a cohesive security infrastructure. This amalgamation ensures that security policies are consistently enforced across disparate systems and applications, eliminating potential vulnerabilities stemming from inconsistencies or lapses in security measures. Through this unified approach, iPaaS fortifies the organizational defenses against a spectrum of cyber threats, ranging from malware and phishing attacks to data breaches and insider threats.
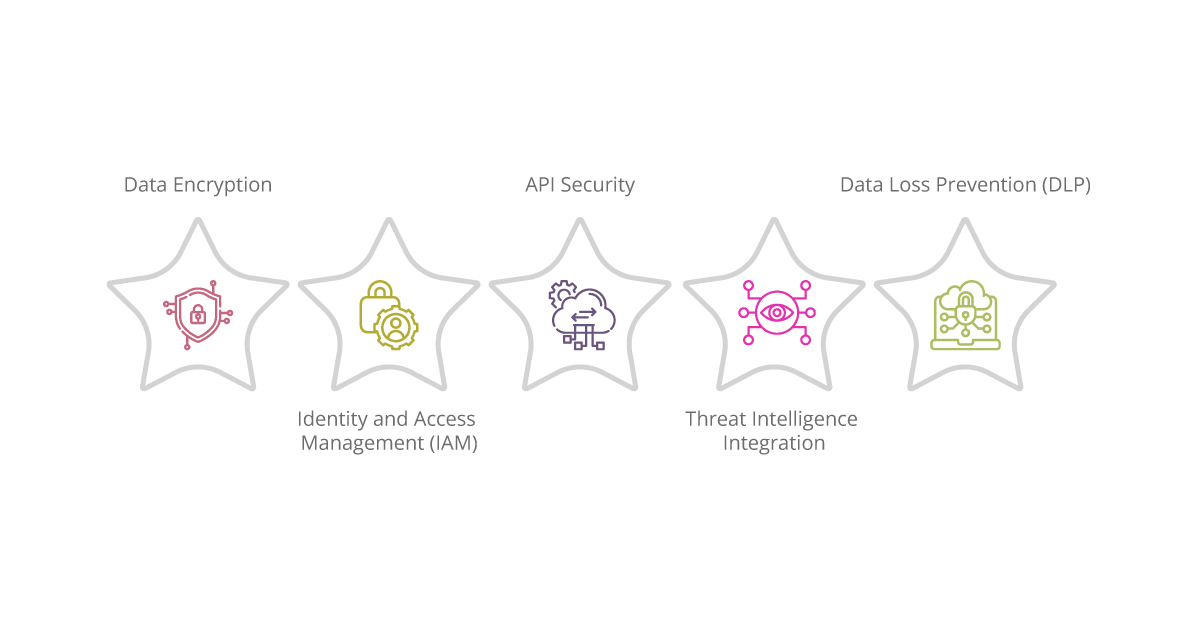
Key Components of iPaaS and Cybersecurity Integration
Data Encryption
Encryption stands as a cornerstone in the realm of cybersecurity, acting as a stalwart guardian of data confidentiality and integrity. Within the iPaaS ecosystem, encryption algorithms are wielded with precision, ensuring that data remains secure both during transit and while at rest. By encoding sensitive information into unreadable cipher text, iPaaS platforms mitigate the risk of unauthorized access or data breaches, fortifying the digital ramparts against potential intrusions.
Identity and Access Management (IAM)
IAM solutions serve as the gatekeepers of organizational resources and applications, regulating user access with meticulous precision. Through the integration of IAM functionalities with iPaaS, businesses can institute a framework of granular access controls, empowering administrators to delineate user privileges with surgical precision. Multi-factor authentication mechanisms further bolster security, requiring users to authenticate their identities through multiple layers of verification, thus erecting an impregnable fortress around critical assets.
Threat Intelligence Integration
The integration of threat intelligence feeds injects a proactive dimension into the iPaaS ecosystem, arming organizations with the foresight to anticipate and counter emerging cyber threats. By harnessing real-time threat data from diverse sources, organizations gain the ability to discern patterns and anomalies indicative of potential security breaches. This wealth of actionable intelligence enables organizations to fortify their defenses, dynamically updating security policies to thwart evolving attack vectors and preemptively neutralize looming threats.
Aonflow is the leading integration platform.
You can kick-start by integrating your first-ever workflow in just a matter of minutes.
API Security
In an era where APIs serve as the lifeblood of digital connectivity, securing these conduits assumes paramount importance. iPaaS platforms deploy robust API security mechanisms, such as OAuth authentication and API key management, to safeguard against unauthorized access and abuse. By fortifying the integrity of APIs, organizations ensure the sanctity of data exchanges between disparate systems, mitigating the risk of breaches stemming from compromised or exploited interfaces.
Data Loss Prevention (DLP)
DLP solutions emerge as custodians of sensitive data, preventing its unauthorized disclosure through vigilant monitoring and control mechanisms. When integrated with iPaaS, DLP capabilities furnish organizations with the means to enforce rigorous data classification policies, categorizing information based on its sensitivity and imposing restrictions accordingly. Real-time monitoring facilitates the timely detection of potential data leaks, enabling organizations to swiftly enact remediation measures and stem the tide of data exfiltration.
Security Information and Event Management (SIEM)
SIEM solutions serve as the nerve center of cybersecurity operations, aggregating and analyzing security event logs from disparate sources to detect and respond to incidents effectively. Through integration with iPaaS, organizations gain the ability to correlate security events across their digital ecosystem, stitching together disparate threads to form a comprehensive tapestry of threat intelligence. Automation of threat detection workflows expedites incident response, enabling organizations to mount a swift and coordinated defense against cyber adversaries.
In essence, the integration of these key components with iPaaS forms the bedrock of a robust cybersecurity infrastructure, empowering organizations to navigate the treacherous waters of the digital realm with confidence and resilience. By fortifying their defenses against a spectrum of cyber threats, organizations ensure the sanctity of their data and the continuity of their operations in an increasingly interconnected world.
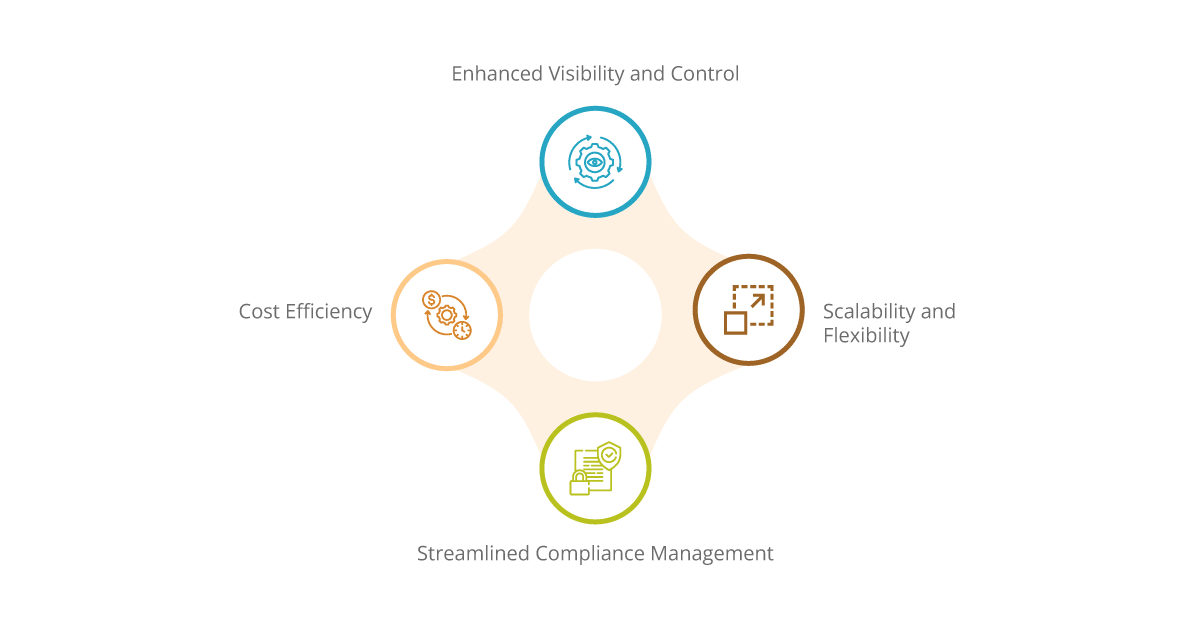
Benefits of iPaaS and Cybersecurity Integration
Enhanced Visibility and Control
Integration of cybersecurity with iPaaS grants organizations a panoramic view of their IT infrastructure, facilitating centralized visibility into data flows and security events. This holistic perspective empowers proactive threat detection, allowing organizations to identify potential security breaches before they escalate. Rapid incident response becomes feasible as security teams are equipped with real-time insights, enabling swift and coordinated actions to mitigate threats. Moreover, the enforcement of security policies is streamlined, ensuring consistent adherence across the organizational landscape.
Streamlined Compliance Management
In an era rife with regulatory mandates such as GDPR, HIPAA, and PCI-DSS, compliance management looms large on the agenda of organizations across diverse industries. iPaaS platforms endowed with built-in compliance features alleviate the burden of adherence by providing robust audit trails, encryption capabilities, and automated reporting functionalities. This seamless integration of compliance measures with iPaaS not only ensures regulatory compliance but also simplifies the auditing process, enabling organizations to navigate the regulatory maze with confidence and ease.
Scalability and Flexibility
The dynamic nature of business demands agility and adaptability from IT infrastructures. iPaaS emerges as a beacon of scalability and flexibility, offering organizations the means to evolve in tandem with changing business requirements and technological landscapes. By seamlessly integrating cybersecurity measures into the iPaaS ecosystem, organizations can scale their security infrastructure proportionally to the growth of their IT environment. This elasticity enables swift adaptation to emerging cybersecurity threats, ensuring that organizational defenses remain robust and resilient in the face of evolving challenges.
Cost Efficiency
Traditional cybersecurity approaches often entail substantial upfront investments in hardware, software, and personnel. In contrast, iPaaS-based cybersecurity solutions present a cost-effective alternative, leveraging the economies of scale inherent in cloud-based infrastructure and subscription-based pricing models. By shifting to an iPaaS-centric cybersecurity paradigm, organizations can reduce capital expenditures, optimize resource utilization, and achieve greater cost efficiency in managing their cybersecurity posture. This judicious allocation of resources not only lowers the total cost of ownership but also enhances the organization’s overall financial resilience in an increasingly competitive landscape.
Conclusion
iPaaS and cybersecurity integration represent a proactive approach to safeguarding IT assets in today’s dynamic threat landscape. By combining the agility and flexibility of iPaaS with robust cybersecurity measures, organizations can strengthen their defenses against cyber threats, streamline integration processes, and ensure the secure transmission of data across their digital ecosystems. As businesses continue to embrace digital transformation, the synergy between iPaaS and cybersecurity will remain instrumental in protecting critical assets and maintaining regulatory compliance in an increasingly interconnected world.
Aonflow iPaaS – Free for First 3 Months!
Build and run up to 1,500 transactions monthly with no cost. No payment info needed!